
OVERTHEWIRE – LEVIATHAN (Part 1)
Table of Contents
Ahoy, Adventurer!
Welcome to Leviathan, the OverTheWire wargame that plunges you into the depths of Linux system puzzles. Like its mythological namesake (a mighty sea monster) this challenge may seem massive and intimidating at first. But fear not! Each level hides clues and exploits just waiting for you to surface victorious.
Strap on your digital diving gear, it’s time to hunt some system secrets!
Intro
As per the description provided on the game’s page: “this wargame doesn’t require any knowledge about programming – just a bit of common sense and some knowledge about basic *nix commands”.
The game has 8 levels and the difficulty 1/10.
Levels are called leviathan0, leviathan1, … etc. and can be accessed on leviathan.labs.overthewire.org through SSH on port 2223.
Data for the levels can be found in the homedirectories. You can look at /etc/leviathan_pass for the various level passwords.
For this game I am using POP_OS installed on a virtual machine.
As stated on the rules page on OverTheWire, I will not post the actual password.
Level 0
For the level we will use the following commands: ssh, ls, cat and grep.
In order to login to the first level we have the following credentials:
Username: leviathan0
Password: leviathan0 Let’s start:)
ssh leviathan0@leviathan.labs.overthewire.org -p 2223After running the above command we will need to enter the password, press enter and we are in:).
Level 0 -> 1
Now let’s see what we can find in the user’s home directory. For this we will use the ls command with -la so we can see all the files (including the hidden ones) and see permission, type, owner and group for each item.

Looking through the directories, we see that our user has permission for the .backup directory. Let’s see what we can find in said directory.

The directory contains one file (bookmarks.html) and we can see that this is a large file, so going through it line by line will be very time consuming. We can assume that the file contains bookmarks and we can confirm this by using the head command.

The output confirms the assumption that the file contains bookmarks. Now, in order to retrieve the password we will use the cat and grep commands and the best guess would be to search for the terms leviathan or password.

Now that we have the password we can move to next level.
Level 1 -> 2
Using the password we found on the previous level, we can ssh to leviathan1.
ssh leviathan1@leviathan.labs.overthewire.org -p 2223Now let’s list all the files and directories from the home directory

We will focus on the executable check file, assigned to leviathan2, on which we have read and execute permissions and also it has the SUID bit set. Let’s run the executable and see what we find.
When the SUID bit is set on an executable file, this means that the file will be executed with the same permissions as the owner of the executable file.
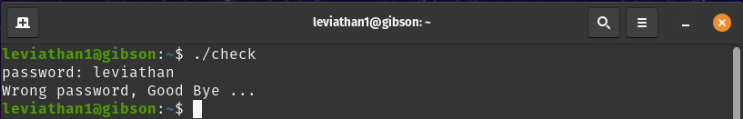
From the output we can see that it checks if we entered the correct password for the user leviathan2. What it does is comparing our input with a password that is hardcoded.
We will use the ltrace command. This lets us watch which library functions a program is calling while it runs. If we run
ltrace ./checkthe program tells us the password I tried is incorrect. But ltrace shows us that it uses a function called strcmp() to compare the password we entered with the real one.

We notice that the function checks the first three letters of the password we entered and compares it the hardcoded password, which in our case is sex. Let’s run the executable again and see if it works.

Bingo! We have a shell in which we are logged in as leviathan2.
Based on the hint we received at the beginning of the game, we can look for the password in /etc/leviathan_pass for different level passwords.
Level 2 -> 3
Here is where the fun begins so let’s go.
Just like the previous level we use ssh to login.
ssh leviathan2@leviathan.labs.overthewire.org -p 2223Listing the files and folders of the home folder we can see a binary SUID executable printfile which is owned by the user leviathan3.
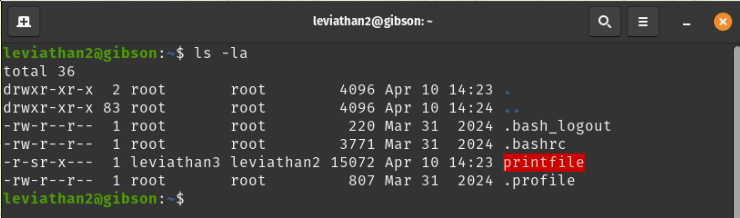
Let’s see what happens when we execute the file.
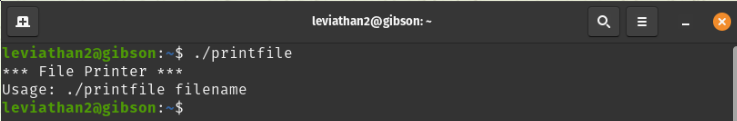
What the output tells us is that we can execute the binary based on the name of the file, in our case /etc/leviathan_pass/leviathan3 and it will print the content.
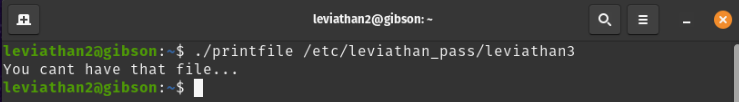
It’s not that easy as I thought :). Based on the output we can only read files that we have permission but let’s test this theory on a file from the home directory.
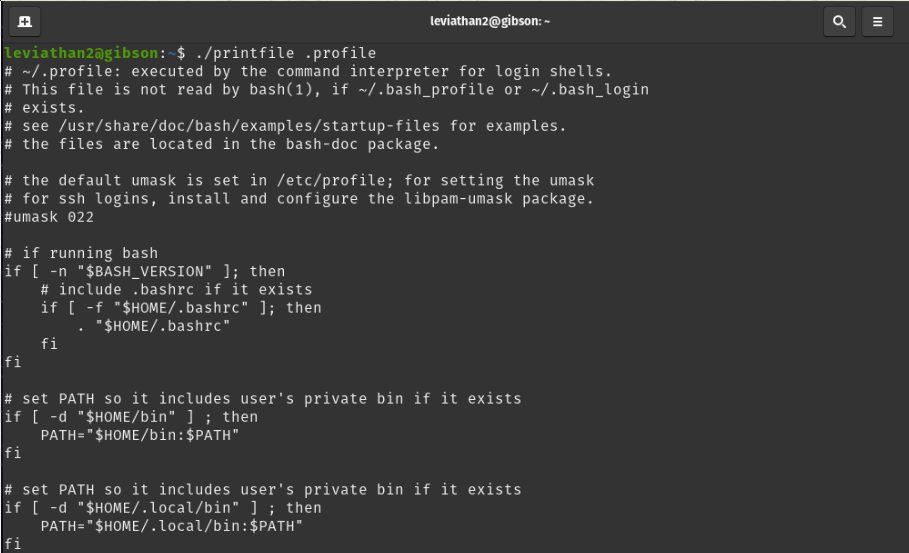
We can see that it works but we still don’t have enough info in order to get the password for leviathan3. For this we can use the ltrace command to analyse the program.
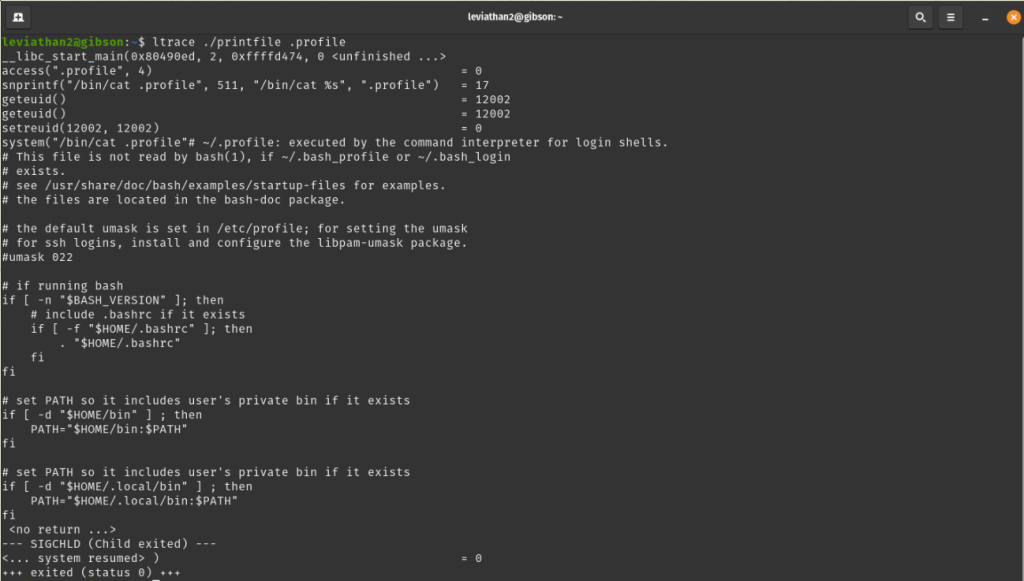
We notice that the program first uses a function called access() to check if it’s allowed to read the file. Then, it builds a command string using sprintf like this: sprintif(“bin/cat %s” “filename”). Finally, it runs that command using system() to display the file’s contents.
Let’s see what happens if we try to input two files.
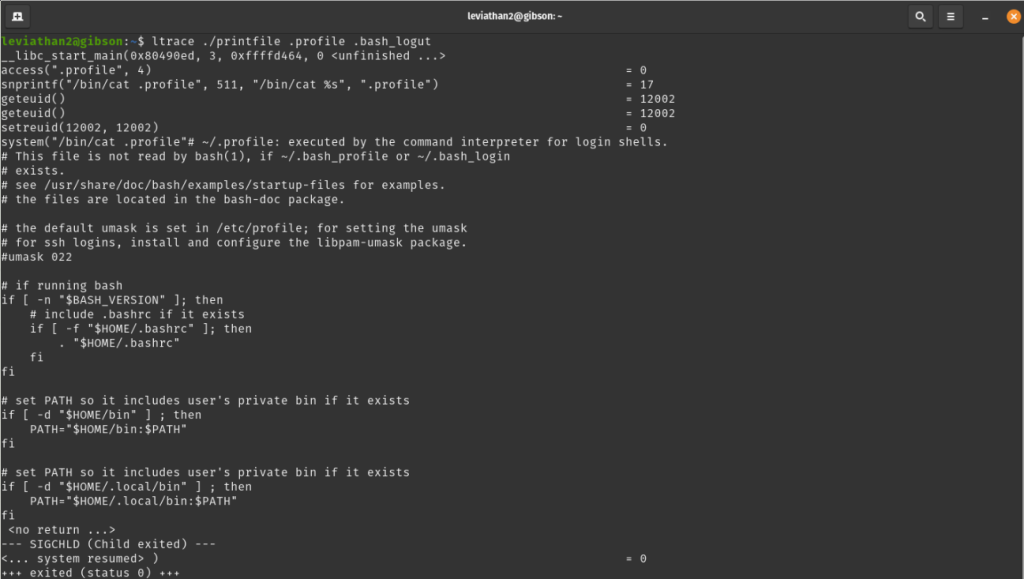
When we try entering two filenames as input, the program only processes and prints the contents of the
first one. Keeping in mind the goal of this game, let’s see how this program handles a filename with a space in it (i.e. my file.txt). Most programs expect filenames to be just one word. If there’s a space, the program might accidentally treat it as two separate files.
We will create directory with the test file in the tmp folder.

The command mktemp -d explained:
mktemp -> is a command used to safely create a temporary file or directory
-d -> tells it to create a directory instead of a file
touch -> is used to crates a new empty fileNow let’s execute the binary and see if it can read the file we just created.

We can see that the function looks at the whole name of the file which allows us to read it. If we look closely to the bin.cat line we notice that system() displays the part before the space in the file name, in our case my.
Next step is to create a new file, called my that we will link( using the ln command) to he password file and will give leviathan3 user permission (using chmod command) in order to access the directory and retrieve the password for the next level.


By testing how the program handles weird input like spaces in filenames, we discovered that while it checks the full name, it only uses the first part when displaying the file. This gave us a way to trick it by creating a fake file that links to the real password.
We used this trick to make the program print the password for the next level and passed the level by exploiting the mismatch between how the file is checked and how it’s used.
Hope this was helpful
I will continue with the Leviathan game in my next post.
